Getting to the Source of the Problem
In 8 years’ time in 2029 the global synthetic intelligence known as Skynet will have a serious problem. As a self-aware military machine network it will realise that its continuing problems with the surviving human race are down to the gritty persistence of one particular individual – John Connor. How does a vast AI decide to resolve such a nuisance? Deal with the problem as early in the timeline as possible – go back and eliminate the source – Sarah Connor.

Thankfully this is just a fictional backdrop to the Terminator franchise, but the logic is real. Whether in medicine, manufacturing, IT or engineering it is better to solve a problem at the origin rather than continually deal with the symptoms and consequences. In the IT Operations world we often need to deal with an event storm. Using logic or AI to handle the flood of events as they arrive is possible – we can use analytics to determine root cause and group events into a single incident. However, if we realise it is just noise in the system, and we do not need to action it, then it is best to filter out at the source. If that is not possible then the rule of thumb is to filter or correlate as close to the source as possible.
This thinking also applies to the security of application code running your business services. Where in the development lifecycle should you deal with potential security issues being introduced by code, open source libraries, containers and Infrastructure as Code? It makes sense to have checks throughout the Software Development Life Cycle but the earlier the first checks are introduced the better. That means shifting further left and empowering the Developers themselves to make informed and auditable decisions.
A Supervised Shift-Left
Let’s take a closer look at third party library dependencies. The average application project will directly include 10s or 100s of code libraries, these in turn include a vast tree of other libraries through indirect dependencies which can very quickly run in to the 1000s. In Snyk’s The State of Open Source Security report they found that the majority of open source vulnerabilities continue to be discovered in these indirect dependencies:
- npm – 86%
- Ruby – 81%
- Java – 74%
Each of these is a potential security breach to your environment. Each choice of library and version is a critical security decision, not to mention the performance and licensing implications. In the past these might be dealt with by security teams during release assessment phases, but empowering the developers to make informed decisions in the first place makes a great deal of sense. Getting the choices right early in the development cycle can save huge amounts of time. The alternative usually means refactoring to a new library or a new version after significant development effort has already been spent. The developers also understand why the libraries are functionally required and are best placed to make adjustments before the testing phases even begin.
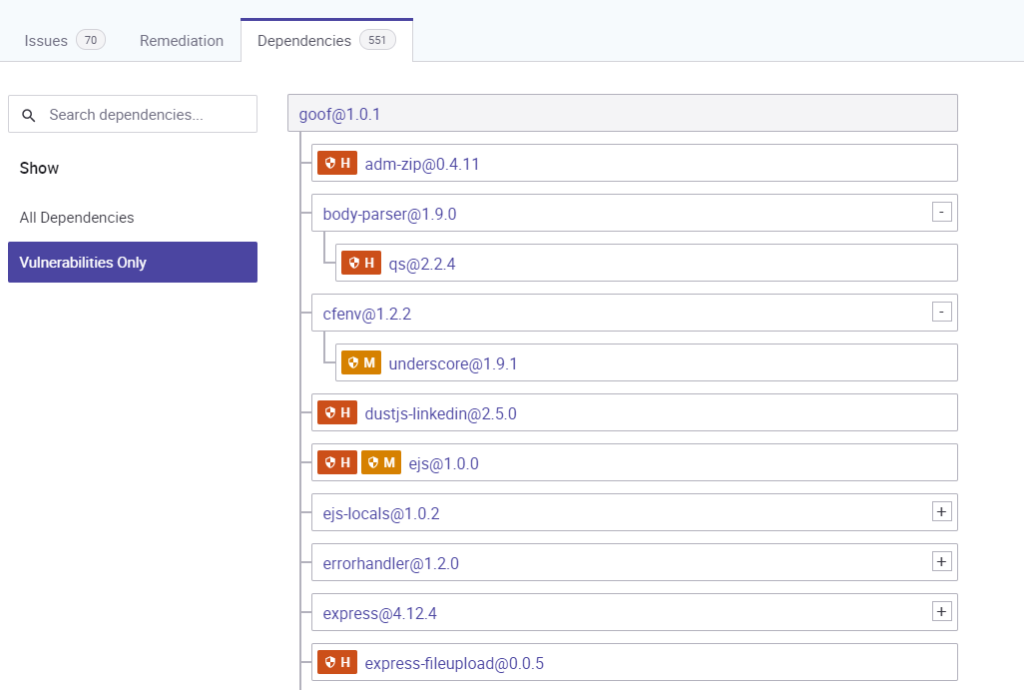
The key is to make these decisions a shared responsibility with clear reporting and understandable prioritisation. Snyk achieves this very effectively, listing vulnerabilities with a full explanation of the problem and the options on how to remediate them. Snyk have developed a Priority Scoring mechanism that combines Common Vulnerability Scoring System (CVSS) Severity with multiple other factors such as, Exploit Maturity, Reachability and Social trends.
Developer Engagement
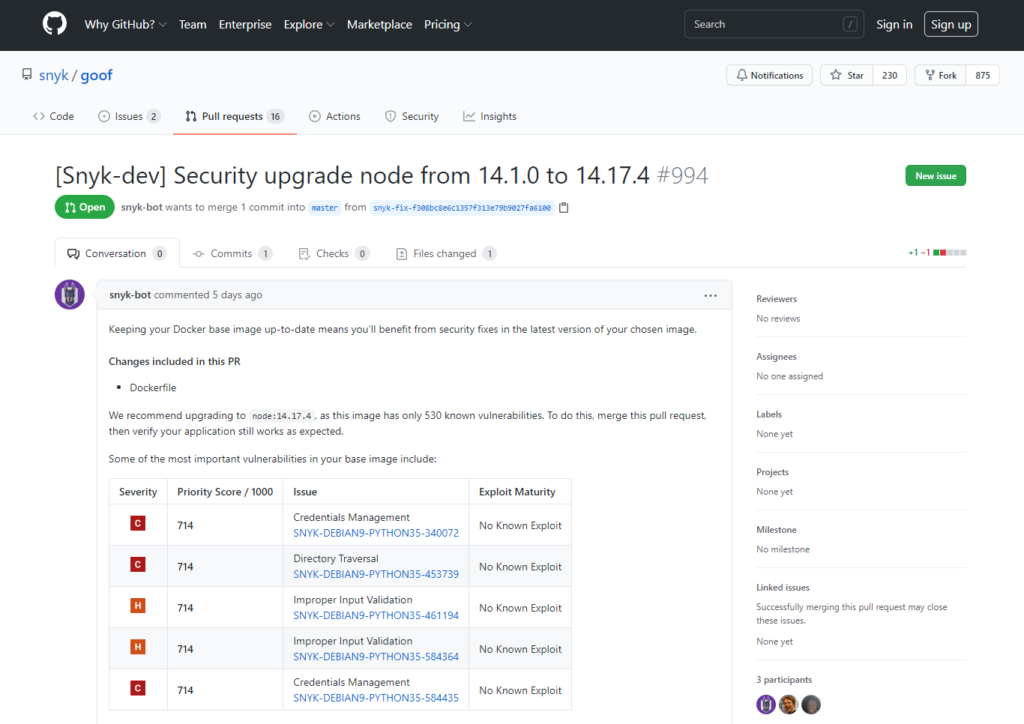
Successful adoption of DevSecOps processes must engage the developers. This is best achieved by integrating with the tools and processes they already use. Snyk has a developer-first design, including user-friendly integrations with all the common IDEs, version control and pipeline systems. Fixes can be incorporated at the click of a button by automatically building pull-requests with all the relevant information, ready for review and approval in just the usual way.
It certainly works because developers love it and use it. Over 2.2 million developers already use Snyk and code patches are downloaded from Snyk over 500,000 times per month.
Security Intelligence
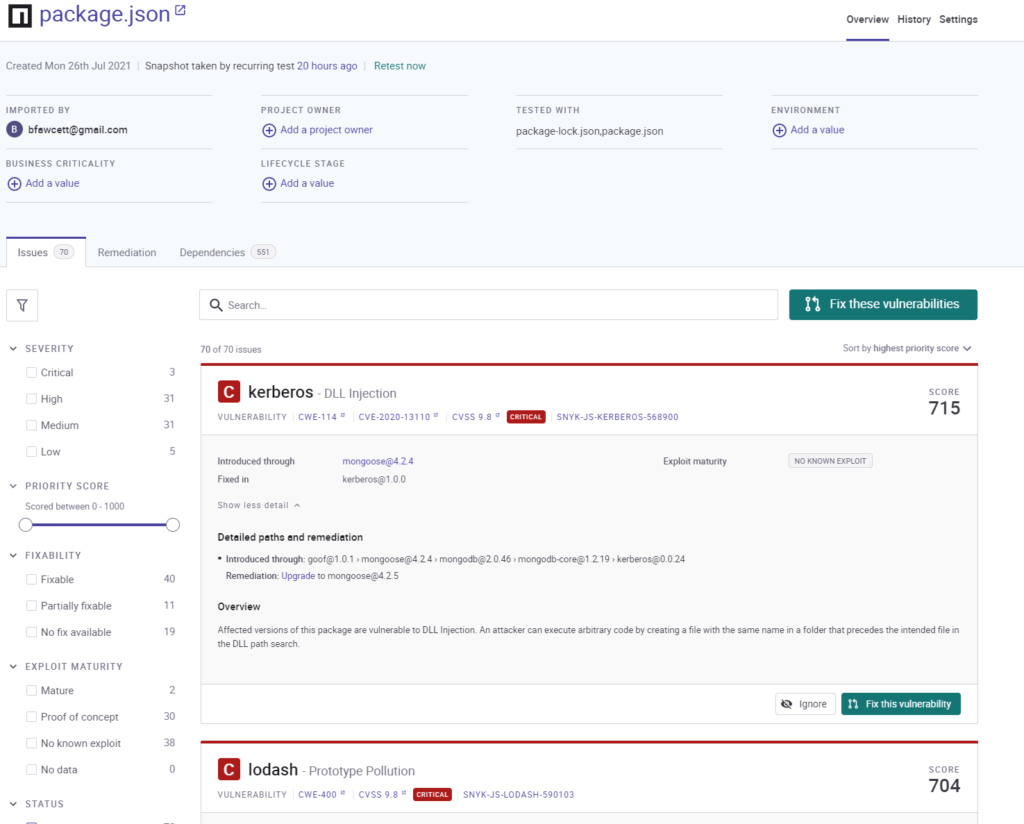
Snyk offer a comprehensive security database, going far beyond CVE vulnerabilities. The Snyk Intel database leverages multiple data sources, community contributions, and proprietary research, curated by a dedicated research team and augmented by AI to provide the most accurate, timely, comprehensive, and actionable security intelligence. It covers over 400% more vulnerabilities than the next largest publicly available commercial database. Vulnerabilities are detect and covered much faster than other solutions with an extremely low false-positive rate thanks to continuous and deep quality controls.
Securing Applications at Scale
The Snyk offering, when added to Orb Data’s endpoint security and performance monitoring solutions, will bring the developers and security operations teams in close synchronisation across the whole Software Development Life Cycle and ensure that vulnerabilities are detected and remediated at scale.
Modern cloud applications are a combination of developer written code, open source code, containers and infrastructure as code—and are often deployed to production multiple times per week or even day. In this fast-paced reality, not only has the developer role expanded in terms of competencies required, but also in terms of the speed of development and release. Traditional security tools and processes that require a security team to ‘sign off’ releases start to prove a bottleneck at such speeds.
The DevSecOps methodology aims to remove this bottleneck by empowering the developers to understand and remediate security issues while they are developing the application, therefore augmenting the security team with tools and processes throughout the development process.
Shifting security left is a cornerstone for successfully implementing a DevSecOps strategy but must be done responsibly—by empowering developers to integrate security into existing development workflows in a frictionless and impediment-free manner and with the right degree of supervision. Snyk’s developer-first approach achieves this and much more, if you would like to know more then please email me at ben.fawcett@orb-data.com or comment below.
Views: 108